
🚀 𝗜𝗻𝘁𝗿𝗼𝗱𝘂𝗰𝗶𝗻𝗴 𝗕𝘆𝘁𝗲𝗖𝗶𝗽𝗵𝗲𝗿’𝘀 𝗔𝗜-𝗣𝗼𝘄𝗲𝗿𝗲𝗱 𝗖𝗖𝗧𝗩 𝗔𝗻𝗼𝗺𝗮𝗹𝘆 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗦𝘆𝘀𝘁𝗲𝗺
At 𝗕𝘆𝘁𝗲𝗖𝗶𝗽𝗵𝗲𝗿 𝗣𝘃𝘁. 𝗟𝘁𝗱., we transform surveillance from passive observation into 𝗶𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝘁, 𝗿𝗲𝗮𝗹-𝘁𝗶𝗺𝗲 𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗺𝗼𝗻𝗶𝘁𝗼𝗿𝗶𝗻𝗴. Traditional CCTV systems only record footage — they don’t understand what’s happening. Our 𝗖𝗖𝗧𝗩 𝗔𝗻𝗼𝗺𝗮𝗹𝘆 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗽𝗿𝗼𝗷𝗲𝗰𝘁 adds a smart AI layer over existing cameras, instantly identifying unusual or suspicious activity, raising alerts, and capturing evidence — all 𝘄𝗶𝘁𝗵𝗼𝘂𝘁 𝗵𝘂𝗺𝗮𝗻 𝗶𝗻𝘁𝗲𝗿𝘃𝗲𝗻𝘁𝗶𝗼𝗻.
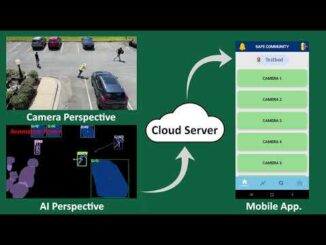
🔹 𝗛𝗼𝘄 𝗜𝘁 𝗪𝗼𝗿𝗸𝘀
Our system is powered by 𝗱𝗲𝗲𝗽 𝗹𝗲𝗮𝗿𝗻𝗶𝗻𝗴 𝘄𝗶𝘁𝗵 𝗣𝘆𝗧𝗼𝗿𝗰𝗵, leveraging the 𝗩𝗶𝗱𝗲𝗼𝗠𝗔𝗘 (𝗠𝗮𝘀𝗸𝗲𝗱 𝗔𝘂𝘁𝗼𝗲𝗻𝗰𝗼𝗱𝗲𝗿) 𝗺𝗼𝗱𝗲𝗹 𝗳𝗶𝗻𝗲-𝘁𝘂𝗻𝗲𝗱 𝗼𝗻 𝘁𝗵𝗲 𝗨𝗖𝗙-𝗖𝗿𝗶𝗺𝗲 𝗱𝗮𝘁𝗮𝘀𝗲𝘁. Here’s the process:
– 𝗙𝗿𝗮𝗺𝗲 𝗘𝘅𝘁𝗿𝗮𝗰𝘁𝗶𝗼𝗻 – CCTV streams are processed frame by frame using 𝗢𝗽𝗲𝗻𝗖𝗩.
– 𝗙𝗲𝗮𝘁𝘂𝗿𝗲 𝗘𝗻𝗰𝗼𝗱𝗶𝗻𝗴 – Frames are converted into high-dimensional feature vectors using the 𝗩𝗶𝗱𝗲𝗼𝗠𝗔𝗘 𝗲𝗻𝗰𝗼𝗱𝗲𝗿..
– 𝗔𝗻𝗼𝗺𝗮𝗹𝘆 𝗖𝗹𝗮𝘀𝘀𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 – The AI detects 14 categories of abnormal activities including theft, assault, fighting, vandalism, accidents, and more.
– 𝗥𝗲𝗮𝗹-𝗧𝗶𝗺𝗲 𝗔𝗹𝗲𝗿𝘁𝘀 – When an anomaly is detected above a confidence threshold, the system triggers immediate 𝗮𝘂𝗱𝗶𝗼 𝗮𝗹𝗮𝗿𝗺𝘀, 𝘀𝗻𝗮𝗽𝘀𝗵𝗼𝘁 𝗰𝗮𝗽𝘁𝘂𝗿𝗲𝘀, 𝗮𝗻𝗱 𝗲𝗺𝗮𝗶𝗹 𝗻𝗼𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀.
– 𝗙𝗹𝗲𝘅𝗶𝗯𝗹𝗲 𝗗𝗲𝗽𝗹𝗼𝘆𝗺𝗲𝗻𝘁 – Optimized for 𝗚𝗣𝗨 𝗮𝗰𝗰𝗲𝗹𝗲𝗿𝗮𝘁𝗶𝗼𝗻 𝘄𝗶𝘁𝗵 𝗖𝗨𝗗𝗔 but can fallback to CPU for cost-effective setups.
🛠 𝗧𝗲𝗰𝗵 𝗦𝘁𝗮𝗰𝗸 & 𝗙𝗲𝗮𝘁𝘂𝗿𝗲𝘀
– 𝗣𝗿𝗼𝗴𝗿𝗮𝗺𝗺𝗶𝗻𝗴 𝗟𝗮𝗻𝗴𝘂𝗮𝗴𝗲: Python 3.x
– 𝗙𝗿𝗮𝗺𝗲𝘄𝗼𝗿𝗸𝘀: PyTorch, Hugging Face Transformers
– 𝗣𝗿𝗲-𝘁𝗿𝗮𝗶𝗻𝗲𝗱 𝗠𝗼𝗱𝗲𝗹: OPear/videomae-large-finetuned-UCF-Crime (VideoMAE)
– 𝗖𝗼𝗺𝗽𝘂𝘁𝗲𝗿 𝗩𝗶𝘀𝗶𝗼𝗻: OpenCV
– 𝗔𝘂𝗱𝗶𝗼 𝗔𝗹𝗲𝗿𝘁𝘀: SoundDevice
– 𝗡𝗼𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀: smtplib (Email)
– 𝗙𝗲𝗮𝘁𝘂𝗿𝗲𝘀: Real-time monitoring, anomaly detection (14 categories), automatic alarms, snapshot/event recording, CPU/GPU fallback.
🌍 𝗦𝗰𝗮𝗹𝗮𝗯𝗶𝗹𝗶𝘁𝘆 & 𝗔𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀
This solution scales across industries:
– 𝗟𝗮𝘄 𝗘𝗻𝗳𝗼𝗿𝗰𝗲𝗺𝗲𝗻𝘁 & 𝗦𝗺𝗮𝗿𝘁 𝗖𝗶𝘁𝗶𝗲𝘀 – Real-time crime response
– 𝗥𝗲𝘁𝗮𝗶𝗹 & 𝗕𝗮𝗻𝗸𝗶𝗻𝗴 – Shoplifting and robbery detection
– 𝗧𝗿𝗮𝗳𝗳𝗶𝗰 & 𝗧𝗿𝗮𝗻𝘀𝗽𝗼𝗿𝘁 – Accident and vandalism monitoring
– 𝗥𝗲𝘀𝗶𝗱𝗲𝗻𝘁𝗶𝗮𝗹 & 𝗜𝗻𝗱𝘂𝘀𝘁𝗿𝗶𝗮𝗹 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 – Burglary and unauthorized access prevention
– 𝗘𝗱𝘂𝗰𝗮𝘁𝗶𝗼𝗻𝗮𝗹 & 𝗛𝗲𝗮𝗹𝘁𝗵𝗰𝗮𝗿𝗲 𝗜𝗻𝘀𝘁𝗶𝘁𝘂𝘁𝗶𝗼𝗻𝘀 – Ensures safety in schools, hospitals, and campuses
💡 𝗪𝗵𝘆 𝗕𝘆𝘁𝗲𝗖𝗶𝗽𝗵𝗲𝗿’𝘀 𝗦𝗼𝗹𝘂𝘁𝗶𝗼𝗻 𝗦𝘁𝗮𝗻𝗱𝘀 𝗢𝘂𝘁
Our system is not just AI-powered — it’s 𝗔𝗜-𝗶𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝘁.. By converting ordinary CCTV cameras into proactive security agents, we help organizations save time, prevent losses, and enhance public safety.
At 𝗕𝘆𝘁𝗲𝗖𝗶𝗽𝗵𝗲𝗿 𝗣𝘃𝘁. 𝗟𝘁𝗱., we don’t just build AI systems — we build 𝘀𝗼𝗹𝘂𝘁𝗶𝗼𝗻𝘀 𝘁𝗵𝗮𝘁 𝗺𝗮𝘁𝘁𝗲𝗿. If you’re looking to bring 𝗶𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲, 𝘀𝗮𝗳𝗲𝘁𝘆, 𝗮𝗻𝗱 𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻 to your surveillance systems, we’re ready to help.
#ByteCipher #ai #deeplearning #computervision #cctv #anomalydetection #pytorch #VideoMAE #smartsecurity #aiforbusiness #innovation #techsolutions



Be the first to comment